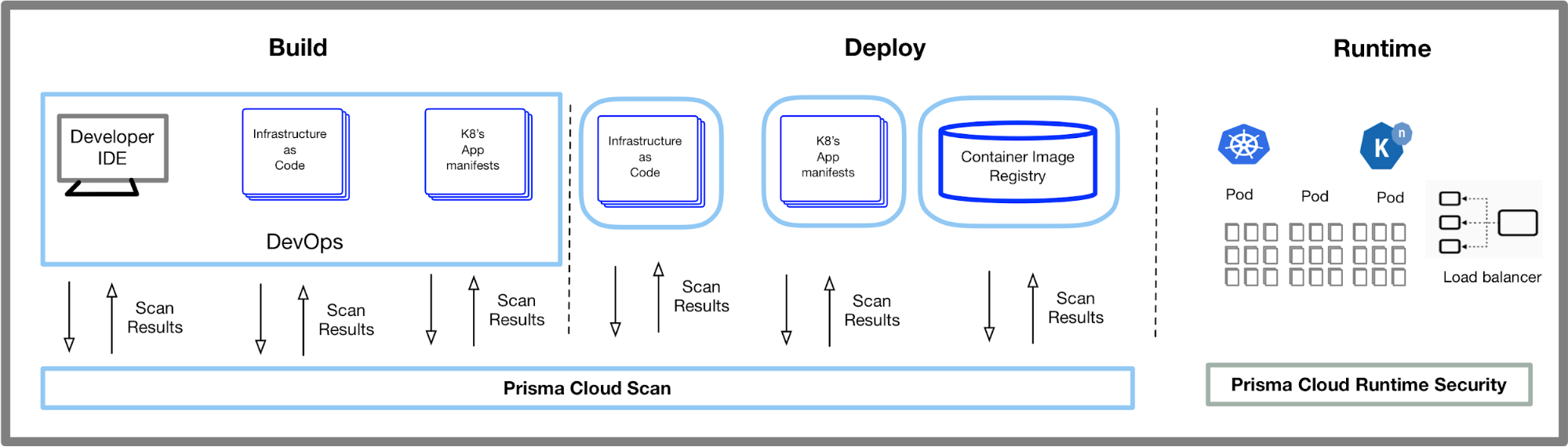
Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog
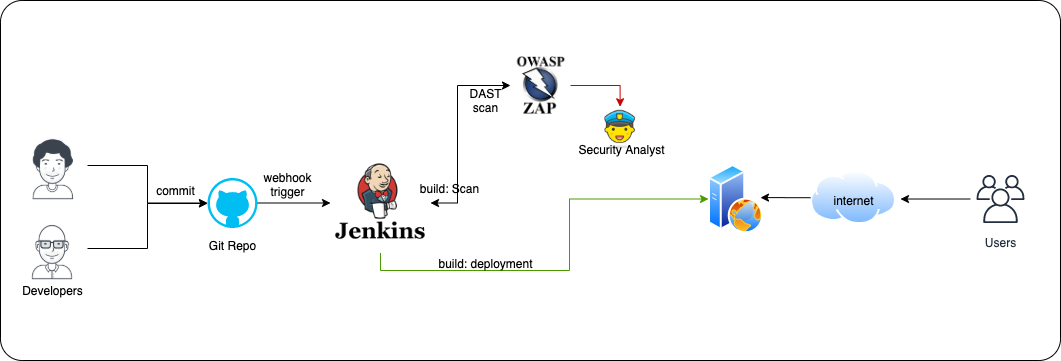
Security in a CI/CD pipeline. Integrate OWASP ZAP into Jenkins CI/CD… | by Olawale Olaleye | CloudAdventure | Medium

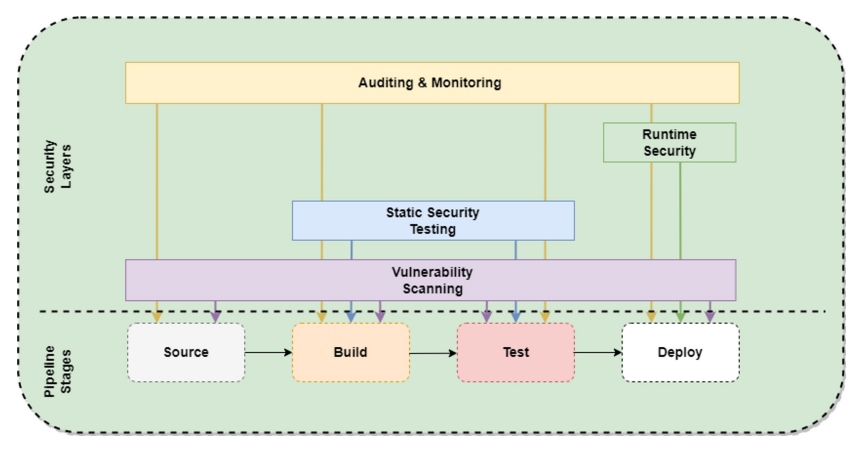
The different stages of a CI/CD pipeline with the emphasis on parallel... | Download Scientific Diagram

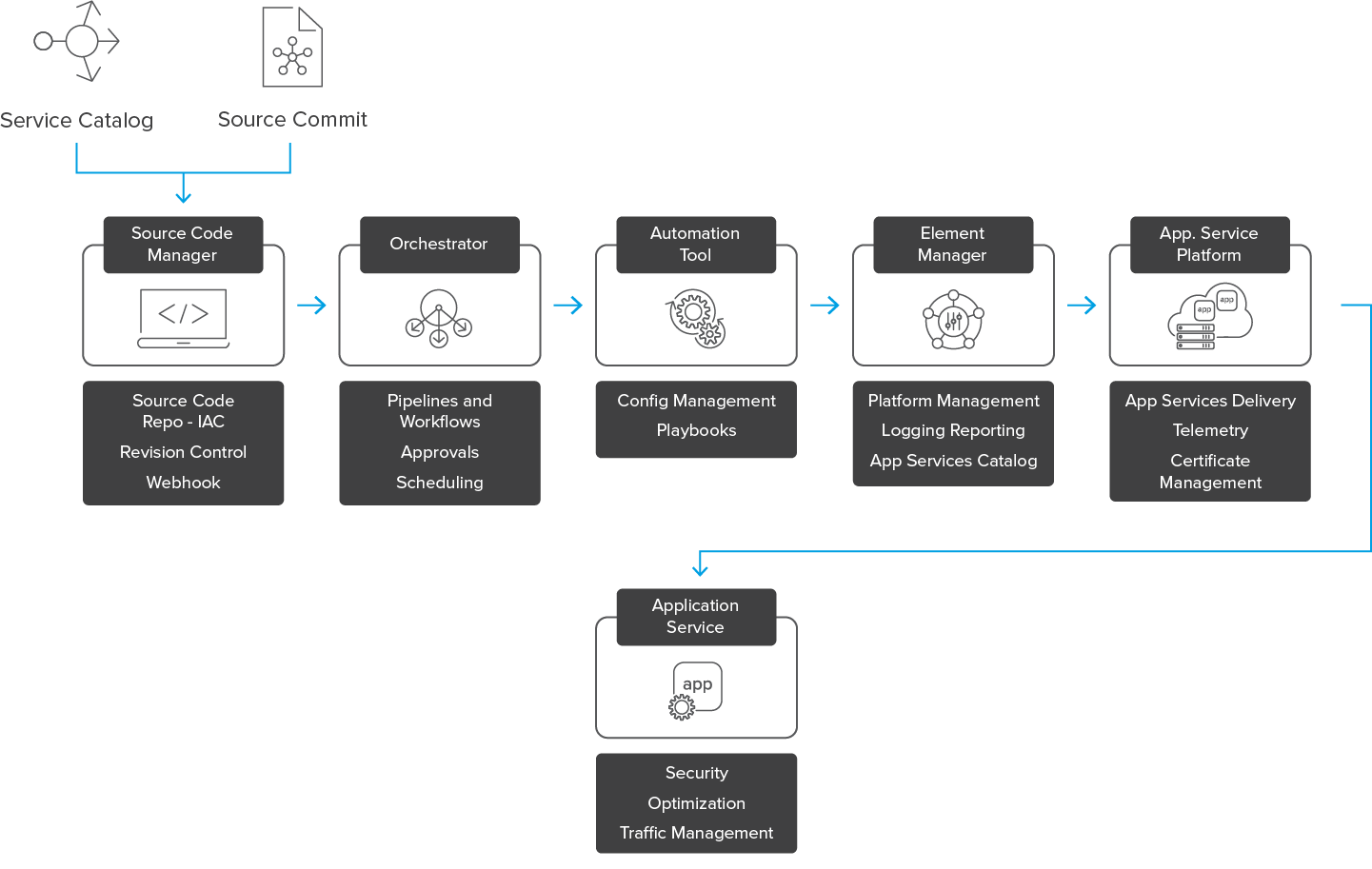
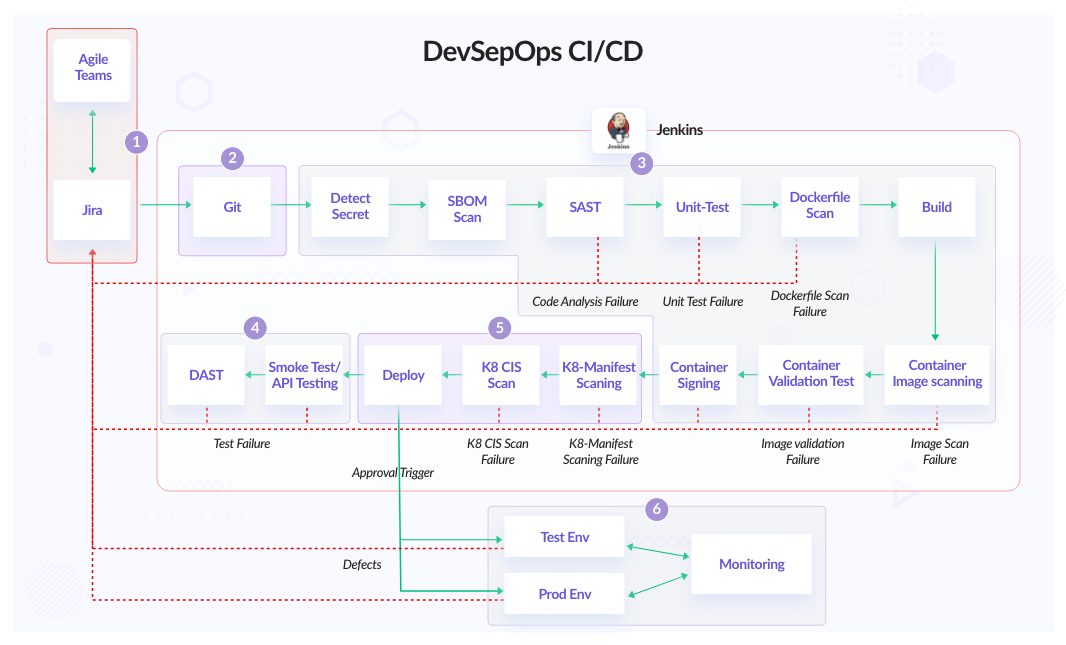



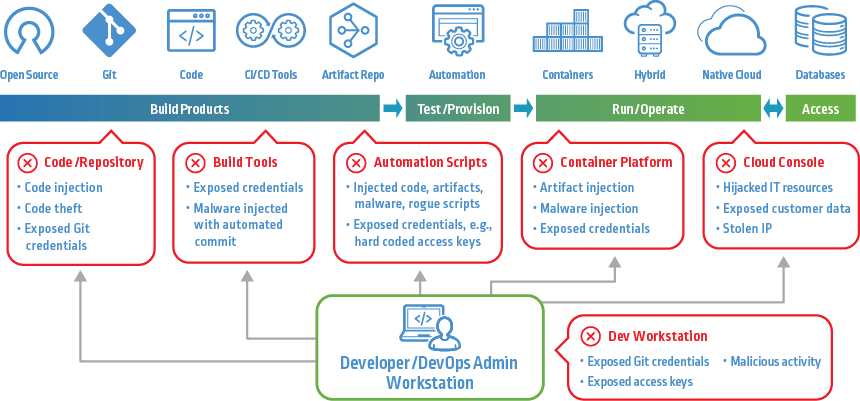




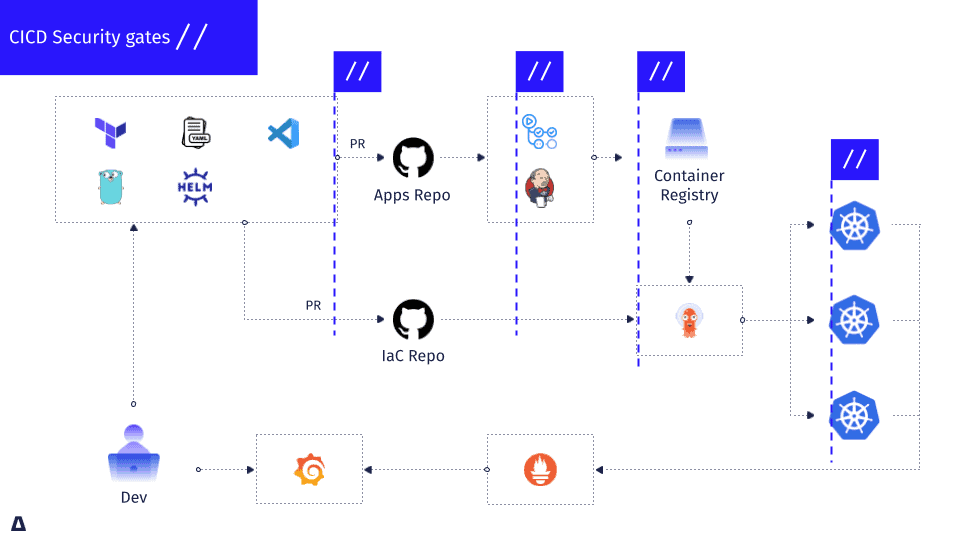
![Compromising CI/CD Pipelines with Leaked Credentials [Security Zines] Compromising CI/CD Pipelines with Leaked Credentials [Security Zines]](https://blog.gitguardian.com/content/images/2022/04/22W15-blog-SecurityZines-Compromising_CICD_pipelinesnal.jpg)