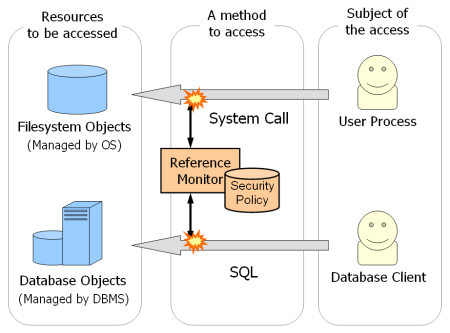
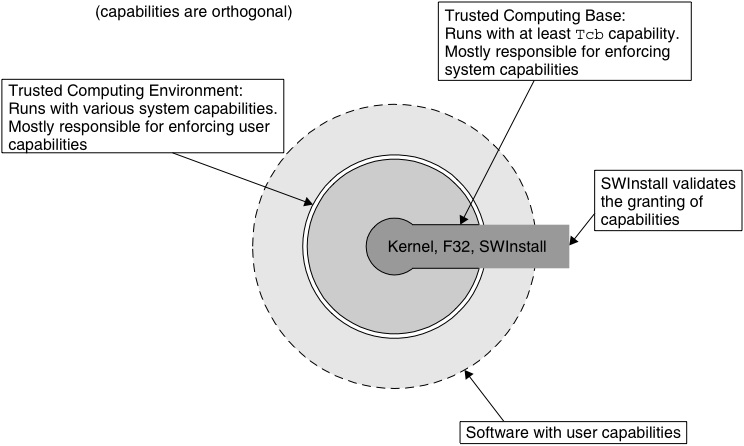
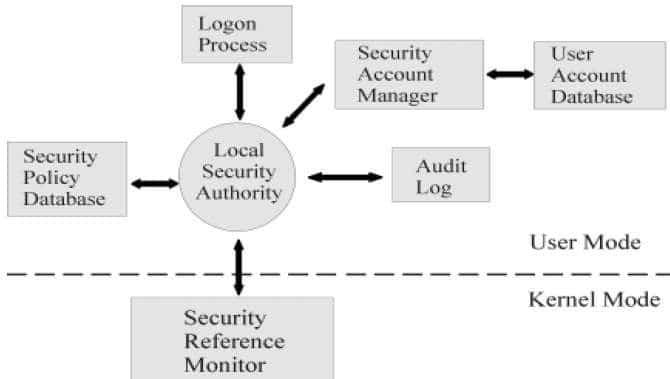
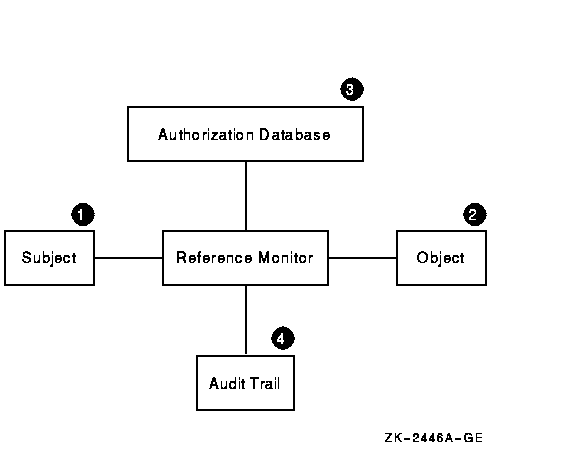
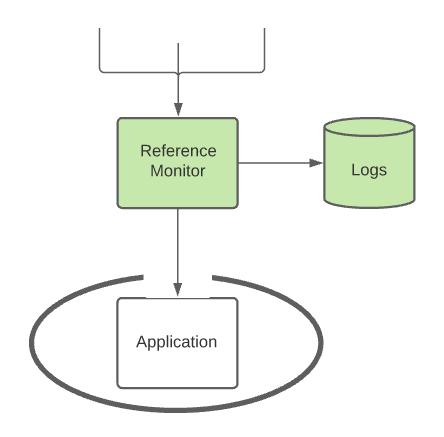
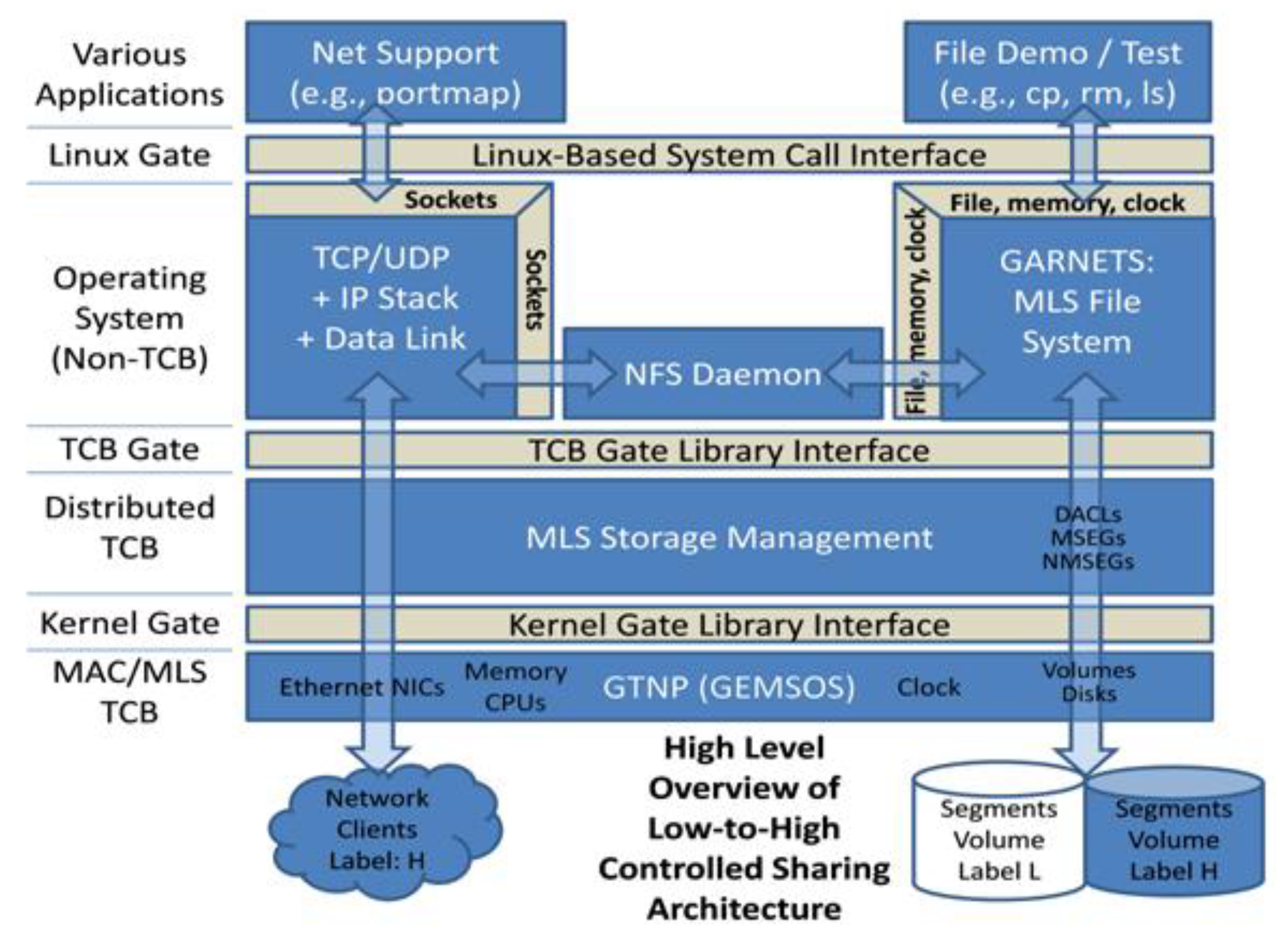
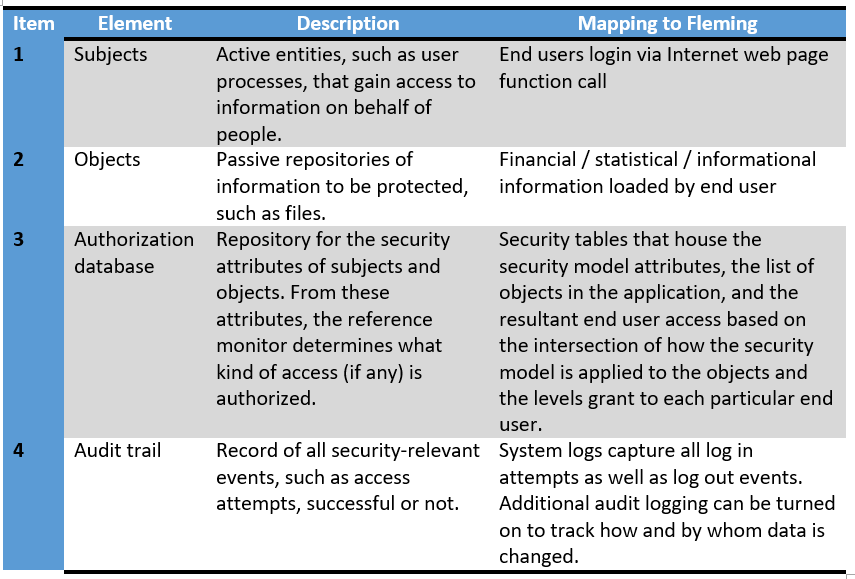
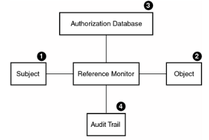
Security kernels implement and enforce the reference monitor concept. The security kernel is used to build the trusted computing system. Security kernels have four main requirements. Which of these is NOT included
GitHub - sailikhithk/security-reference-monitor: Seattle Reference Monitor implementation and its attack cases and improvements