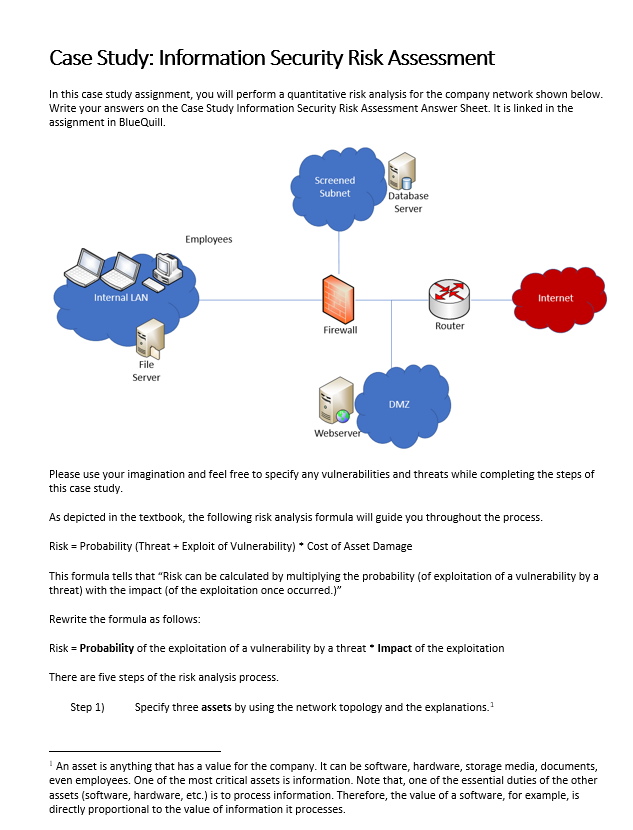
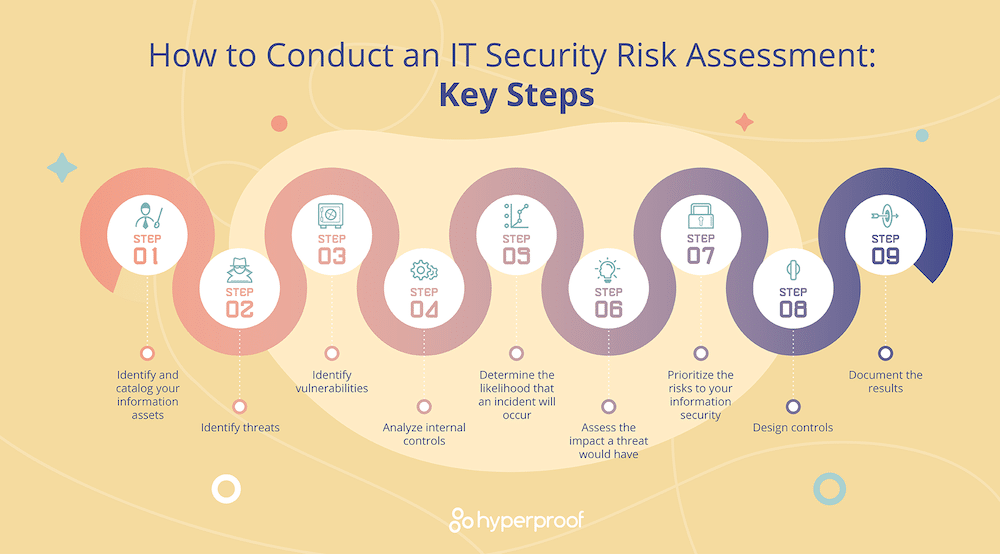
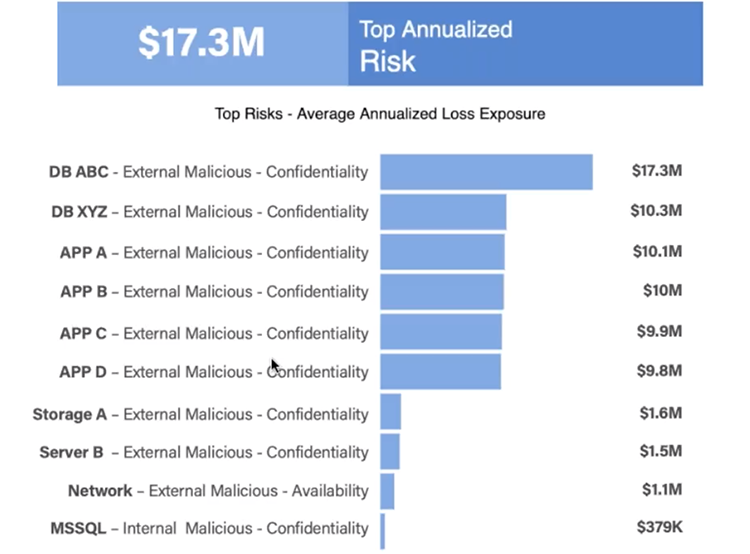
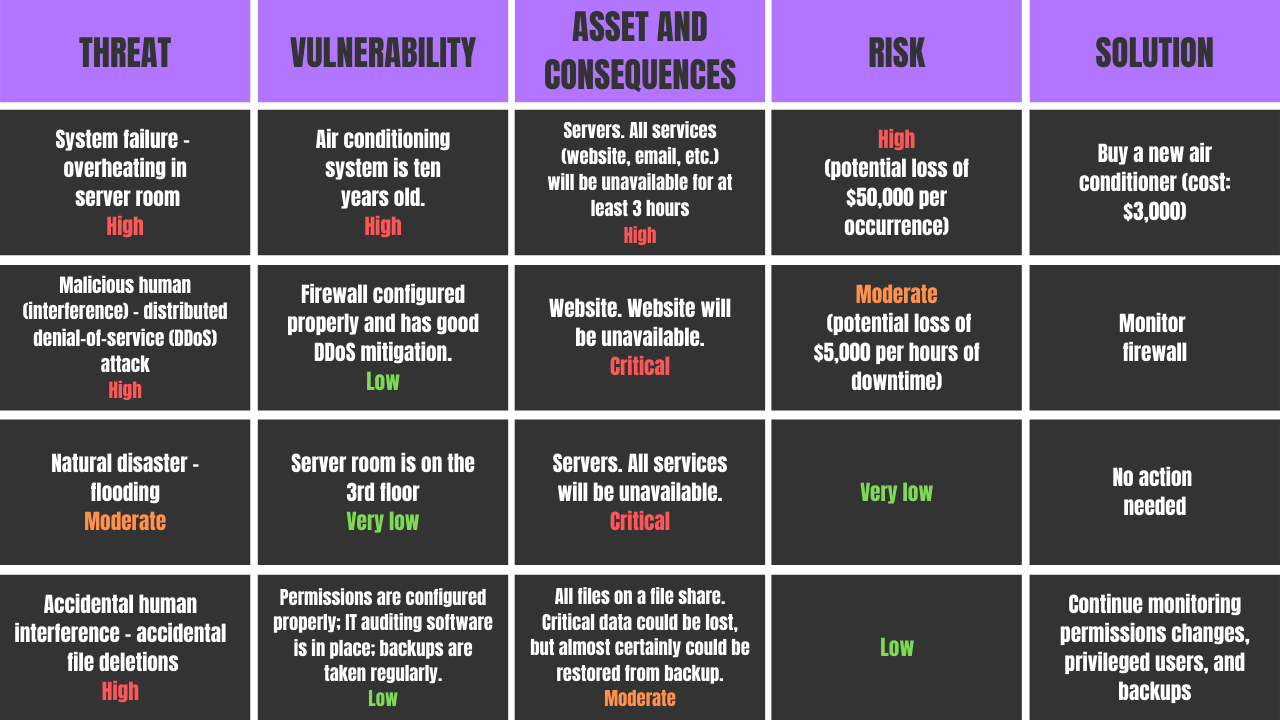
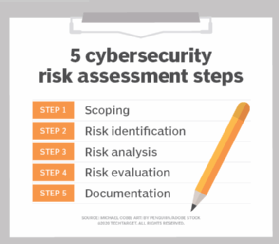
Information Security Risk Assessment in Healthcare: The Experience of an Italian Paediatric Hospital | Semantic Scholar
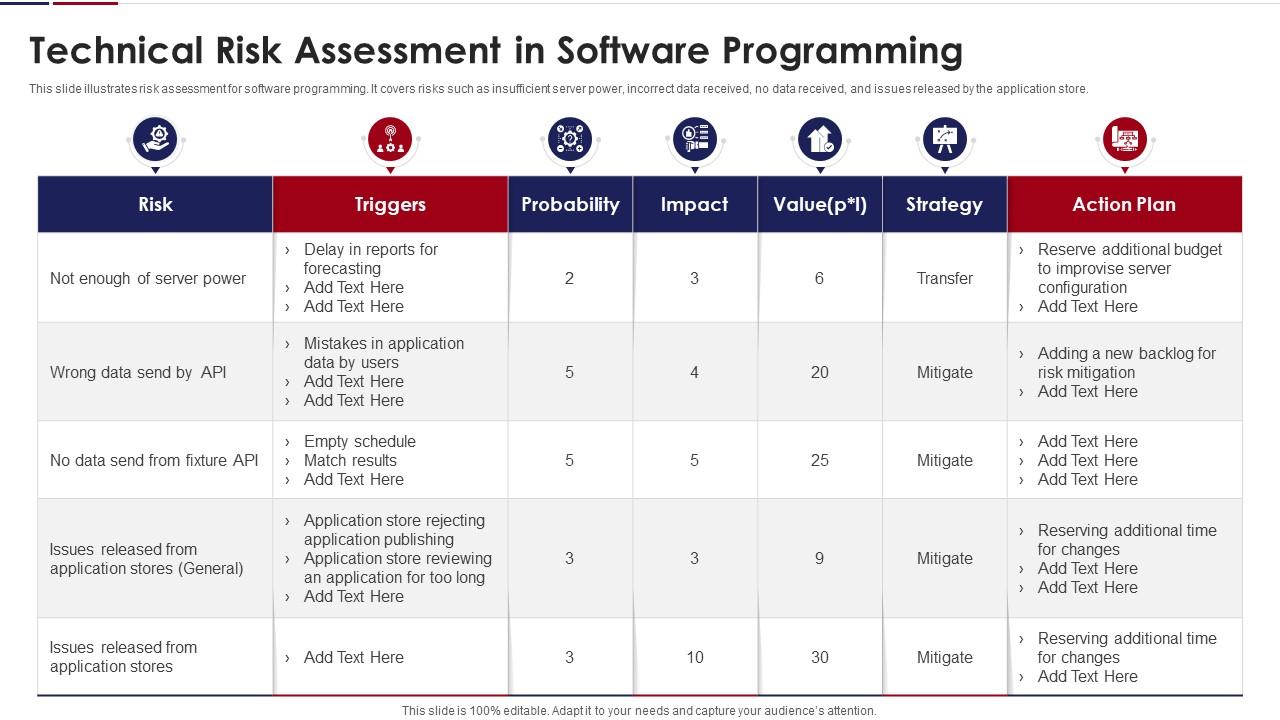
Technical Risk Assessment In Software Programming | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
![PDF] Development of a Web based Decision Support System for trans-boundary environmental risk assessment and management | Semantic Scholar PDF] Development of a Web based Decision Support System for trans-boundary environmental risk assessment and management | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b92f4e4477a7a4249fa8edbe1ff029b92789a1b9/4-Figure1-1.png)
PDF] Development of a Web based Decision Support System for trans-boundary environmental risk assessment and management | Semantic Scholar
Internet Security Risk Assessment Report With Vulnerability And Impact Ppt PowerPoint Presentation Icon Backgrounds PDF - PowerPoint Templates

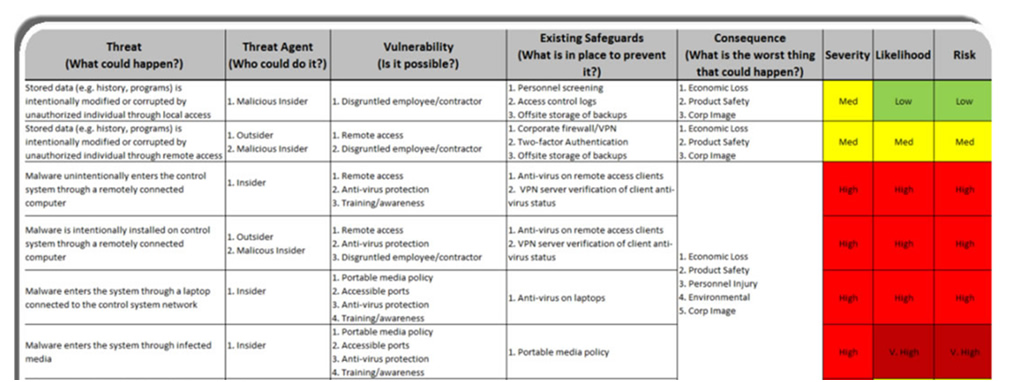

![Risk management concepts and the CISSP (Part 2) [Updated 2022] | Infosec Resources Risk management concepts and the CISSP (Part 2) [Updated 2022] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2020/10/Screen-Shot-2017-01-05-at-11.56.36-AM.png)